Contents
- Overview
- System Requirements
- Installation and Setup
- Components
- Overview
- Usage
- Introspect UI
- Software Download
Introduction
The Introspect application monitors access to users' privacy sensitive files and notifies the user when a process having read any of those files attempts network access. Notification allows the user to grant or deny network access.System Requirements
We recommend a system with at least Core i5 Intel® processors, Intel Corporation, Santa Clara, CA, USA, or AMD® equivalents, Advanced Micro Devices, Inc., Santa Clara, CA, with at least 8 GB of RAM memory, and a powerful GPU (graphics card) such as NVIDIA® GTX 970, NVIDIA Corporation, Santa Clara, CA, or AMD R9 290 equivalents or greater.
The Introspect™ app was developed and tested on Windows 11®, Windows 11 is an operating system produced by Microsoft Corporation, Redmond, Washington and is currently only available for Windows 11 running in test signed mode.
Installation and Setup
You will need to use a Windows computer setup in test signed mode in order to run this system. This restriction may change in the future depending upon the level of interest in this system. Type cmd in the search bar to locate Command Prompt and right-click on it to choose Run as administrator. Switch on test mode using the following commands:
bcdedit.exe -set TESTSIGNING ONFollow the instructions, and when complete, there will be a message saying that Test Mode is activated in the lower-right corner of the screen.
Extract the installation files from the introspect.cab file in a directory of your choosing. The introspect.cab file is available for download from our website. Its signed, so make sure to verify the digital signature after download to ensure that you have an unmodified copy of the file. The signature can be verified by right clicking on the file and choosing the Properties menu. Open the explorer to the install directory, and right click on the introspect.inf file, and choose the install option. After the installation is completed, using the command prompt, start the two kernel services with the following commands:
fltmc load introspect net start inspect
The first command starts the file system monitoring service and the second command starts the network monitoring service. These kernel services can also be stopped at any time with the following commands:
fltmc unload introspect net stop inspect
Next, start the Introspect application using the following command:
introspect.exe
Introspect can be stopped at any time by exiting the application. Exiting the application causes monitoring and notification to stop, and network traffic to flow normally per system and firewall settings.
Components
The Introspect application is comprised of three parts; two of which run in the Windows® kernel and one user application.
Kernel
The kernel components monitor file system and network activity.
Introspect
The Introspect kernel service monitors file system activity on the computer. It focuses is on file system reads and writes, reporting back to the user application. Processes having read sensitive files are flagged. Any files subsequently written by these processes are automatically marked as privacy sensitive.
Inspect
The Inspect kernel service monitors network activity, intercepting attempts by processes to transmit data. It relays such attempts back to the user application which reviews which files a process has read. Processes having read privacy sensitive files are flagged and the user is notified of the transmission attempt. Users can then decide whether to allow or deny the transmission. Decisions are remembered for any future attempts by the same process. Decisions are cleared once the process terminates.
User
The Introspect application runs on the desktop and continuously received data from the kernel components monitoring file system and network activity.
Introspect App
The Introspect application displays activity reported by the kernel components. It allows users to intervene in order to allow or deny network access to system processes having read privacy sensitive files.
Overview
Communicating with the two kernel processes, the Introspect application monitors activity on the file system and network. Processes that have read privacy sensitive files that are accessing the network are interrupted and reported to the end user by the Introspect application. A popup windows alerts the user, and the end user has the choice to grant or block network access for the process.
We now cover how to launch and deploy the Introspect application.
Usage
As mentioned in the system setup section above, using a command shell in administrative mode, start both kernel services followed by the Introspect user application using the three commands shown here:
fltmc load introspect net start inspect introspect.exe
Do not stop the kernel services before the UI application has terminated.
A screen shot of the application upon successful startup is shown in Figure 1.
UI
The Introspect User Interface (UI) is shown in Figure 1. It is comprised of several areas, each of which can be closed by clicking on its close button. Once closed, the area can be recovered by using the View menu at the top of the frame, the choosing Toolbars and Windows and finally selecting the area to be recovered. We will now go over each of the areas of the interface.
Files
The Files area appears on the left of the frame. It can be toggled between the Files View and Mark View by clicking on the tab at the bottom of the area. The purpose of both views is to allow the user to select and mark privacy sensitive files.
File View
The File View displays the contents of the internal non removable file systems; similarly to other applications that present a hierarchical view of internal storage. The user can right click on either an individual file or directory, and choose the Mark menu item to identify the file or directory as privacy sensitive. If a directory is marked as privacy sensitive, then its contents are indirectly also privacy sensitive. Marked items can be unmarked by choosing the corresponding menu option. Color codes indicate marked items; marked files appear in red and marked directories appear in blue.
Files that are locked or currently in use may not appear in the File View. Close all opened files and refresh the File View to show any missing files.
Mark View
The Mark View is similar to the File View above, but focuses only on marked areas of the file system; making it easier to review which files are marked.
Main Area
The Introspect application hosts three views in the center of the frame; each accessible by clicking on its corresponding tab at the top of the screen.
Main View
The Main View is shown at startup and presented in Figure 1. The Main View is a 3D view of the processes running on the system; each represented by a sphere. The process id (or number) is shown on each sphere. A process having read a file marked as privacy sensitive has a disk object above it. One such process appears at the back of the 3D display in Figure 1. If the same process subsequently writes to a file, it is also shown with a disk object below it. Once a process has read a privacy sensitive file, any writes by that process are marked as privacy sensitive; the process may have included some or all of the privacy sensitive information in the files it has written. Subsequent reads of these files by any other process are marked as privacy sensitive. The Main View is mostly informative of ongoing system activity.
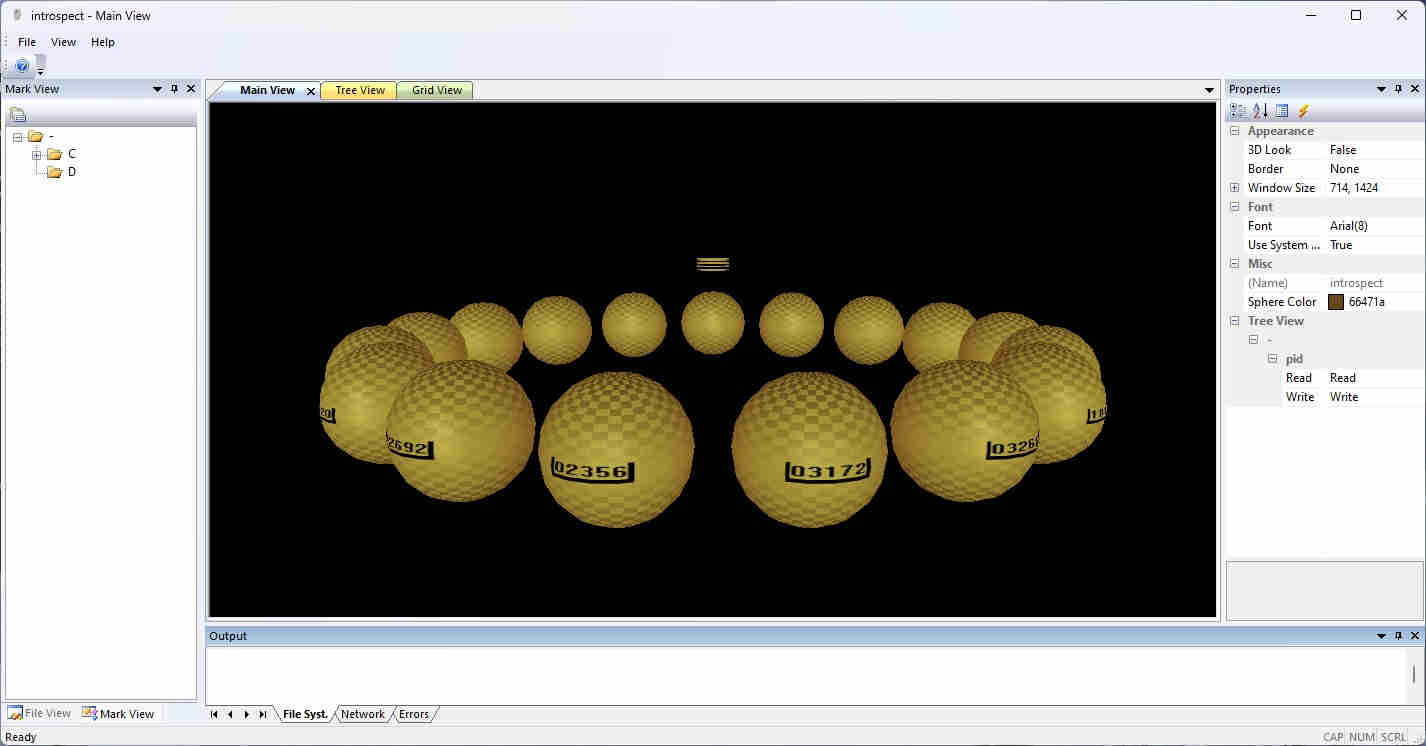
Tree View
The screen shot shown in Figure 2 displays the Tree View; accessible by selecting the corresponding tab at the top of the frame. The Tree View focuses specifically on processes having read and possibly subsequently written privacy sensitive files. The process identifier or number is shown following the root of the tree. Process subitems identify the files that have been read and written by the process.
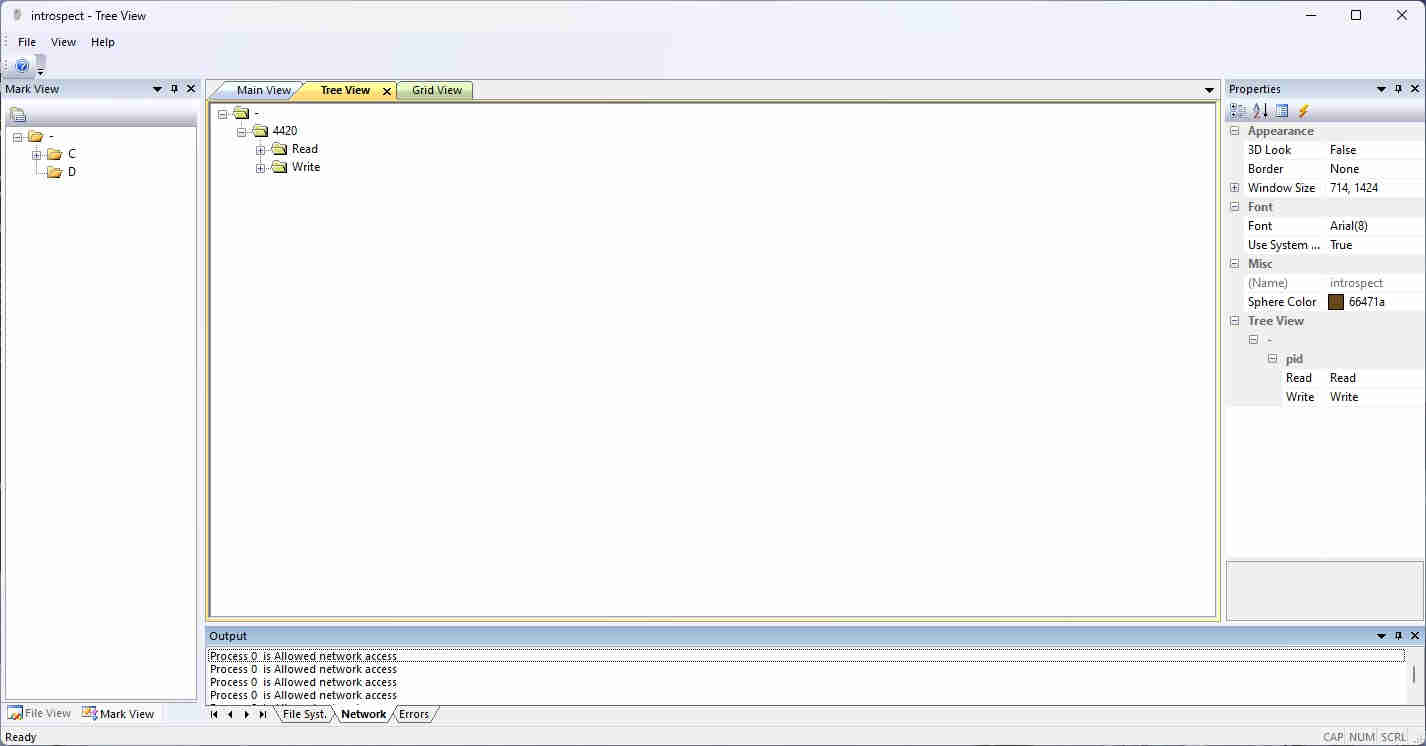
Grid View
The screen shot in Figure 3 displays the Grid View. This information is stored in a SQLite database located in the user's AppData folder (e.g., C:\Users\Jane\AppData\Roaming\softsystr\introspect\default.db). The Grid View is a table that lists all privacy sensitive files contained in the system. These files appear as a result of the user having identified them as privacy sensitive, or as a result of a process writing a file after having read a privacy sensitive file. Only files written to internal storage appear in the grid. A warning is issued for files written to removable storage. The warning message appears in the error window. If the last column in the list, source id is blank, then the file is privacy sensitive as a result of user intervention. If instead it has a number, then it is the result of a process having written the file after reading a privacy sensitive file. The row with the matching id column identifies the privacy sensitive file that was read by the process.
The user can examine these written file in order to validate that they do or do not contain privacy sensitive information. If not, they can be purged from the list by right clicking on the matching volume id column of a row and selecting the delete menu option.
Properties
The Properties area appears at the right of the frame and has options that allow the user to customize the appearance of the Introspect application.
Output Area
The output area is at the bottom of the frame, and displays continuous data feeds from the two kernel services. The output area can be seen in Figure 3.
File System
The first tab shows the continuous data feed from the file system monitor. This tab is useful to gauge the amount of file system activity.
Network
The second tab shows the feed from the network activity monitor, including whether traffic is allowed or denied. This tab is useful to gauge the amount of network activity.
Errors
The third tab displays any errors encountered while accessing the continuous feeds.
Software Download
We request that you contact us to obtain a user login which is required in order to access the download link. The Introspect system is presently a Limited Availability Beta. It's only available for 64 bit versions of Windows 11™, and currently runs only in test signing mode for trial purposes. We plan on making it available for regular install depending upon interest. We are interested in clients from diverse sectors, academia, and welcome feedback regarding features and function.
